< Back to insights
Published 14. Jun. 2021
Monica Verma, CISO of Helsedirektoratet: The Necessity of Resilience and How to Embed it in Your Organization
Monica Verma explains how organizations can arm themselves with long-term cyber resilience plans to combat future threats.
The rising number of cyber attacks has caused IT leaders across industries to take cybersecurity measures more seriously than ever before. This is reflected in our interviews with CIOs on cybersecurity investments who revealed cloud security and cybersecurity strategies as top priorities. A number of industries have also adopted digital twins to protect their digital assets, allowing cyber security platforms to perform at higher efficiency and accuracy.
However, CIOs and CISOs face continuous challenges with implementing high-level cybersecurity due to limited budget and online security obstacles in a hybrid workforce.
Monica Verma, CISO of Helsedirektoratet, podcast host of We Talk Cyber, and blogger on MonicaTalksCyber.com, shares valuable insights on operational and cyber resilience, effective cybersecurity programs for critical infrastructure, the evolution of the CISO role, and more.
What are your top cybersecurity lessons learnt from the pandemic?
There’s no absolute security. Things can and will go wrong. That’s true for both a pandemic and a cybersecurity crisis. The pandemic has shown us an increasing need for adaptive security as a part of building resilience and crisis management.
Operational resilience is as much dependent on the human and communications aspect as the technical capabilities in place. It’s not a matter of “if”. It’s no longer even a matter of “when”. It’s a matter of:
- How long ago did attackers infiltrate?
- How quickly can/did we detect it?
- How quickly and effectively can we respond?
- How do we handle the unknowns?
- How do we adapt and continue critical services?
Preventive controls are not enough. Effective crisis management requires planning for both the known-unknowns and the unknown-unknowns.
How do you think the role of CIO/CISO has evolved in terms of ensuring the security of their organization?
Traditionally, the CISO role started as a technical role — a younger sibling or a distant cousin of the C-Suite. It’s mostly a title associated with a lack of budget, mandate, or even a seat at the grown-ups’ table.
However, an effective CISO role is that of a business leader itself, an advisor to the board, top management, and the rest of the business. The role has evolved from a “glorified” security engineer to a business and organizational advisor. As data breaches and ransomware attacks have skyrocketed recently, particularly during the pandemic, more organizations look up to the CISO to help them identify, understand and manage their threats and risks better.
Today, many organizations understand that a CISO’s job is not just to build an information security management system (ISMS) with a bunch of policies and other governing documents. Organizations are beginning to employ a CISO/CIO to rather effectively invest in security with timely risk management and provide sound advice tailored to the stakeholders.
As a result of this evolution, there’s also been a shift in the skills required to be an effective CISO:
- Professional skills such as risk advisory and business understanding, which span very well outside the technical realm, and;
- Soft skills such as concise, clear, and effective communication, are a driving force behind the vision and strategy of an effective leader.
There are many organizations that still see and employ a CISO role as a technical role, but we are seeing a shift in terms of budget, investments, and better mandate — transforming the CISO into a cross-functional advisory role worthy of an actual seat at the table.
Today’s organizations have a higher risk of exposure due to a more complex and global digital footprint. What strategies can organizations implement to better prepare for cyber attacks?
There are three critical aspects that need to be addressed in order to better manage the ever-increasing risk exposure and ever-complex digital footprint:
a. Always have a holistic view of both the current state within the organization and its supply chain as a fundamental input to your cybersecurity strategy. You are as strong as your weakest link. It’s not your employees. It’s the weakest link in your entire supply chain. You need to be aware of the weakest link in your supply chain, in order to be better prepared for cyberattacks.
b. Always have a risk-based approach when developing your strategy, operationalizing your cybersecurity plan, and investing in security controls (people, process, and technology). Your organization’s risk profile is affected by other risk profiles in your entire supply chain. A risk-based supplier management is as important as a risk-based security governance within your organization. Additionally, an effective risk-based approach will also take into account the threat landscape.
c. Balance your security investment effectively between preventive controls, predictive controls, and adaptive and other response controls, based on your risk exposure. The more critical data, services, and infrastructure you have, the higher your exposure in case of a cyberattack. It’s the difference between an e-commerce website going down for weeks vs. critical data or service not available for even a few hours or days. Preventive controls and cyber hygiene are a must. But as there is no 100% security, these will fail. Your cybersecurity strategy must take into account effective crisis management and building operational resilience over time.
Based on your cybersecurity adoption lifecycle model, how can an organization build cyber and operational resilience?
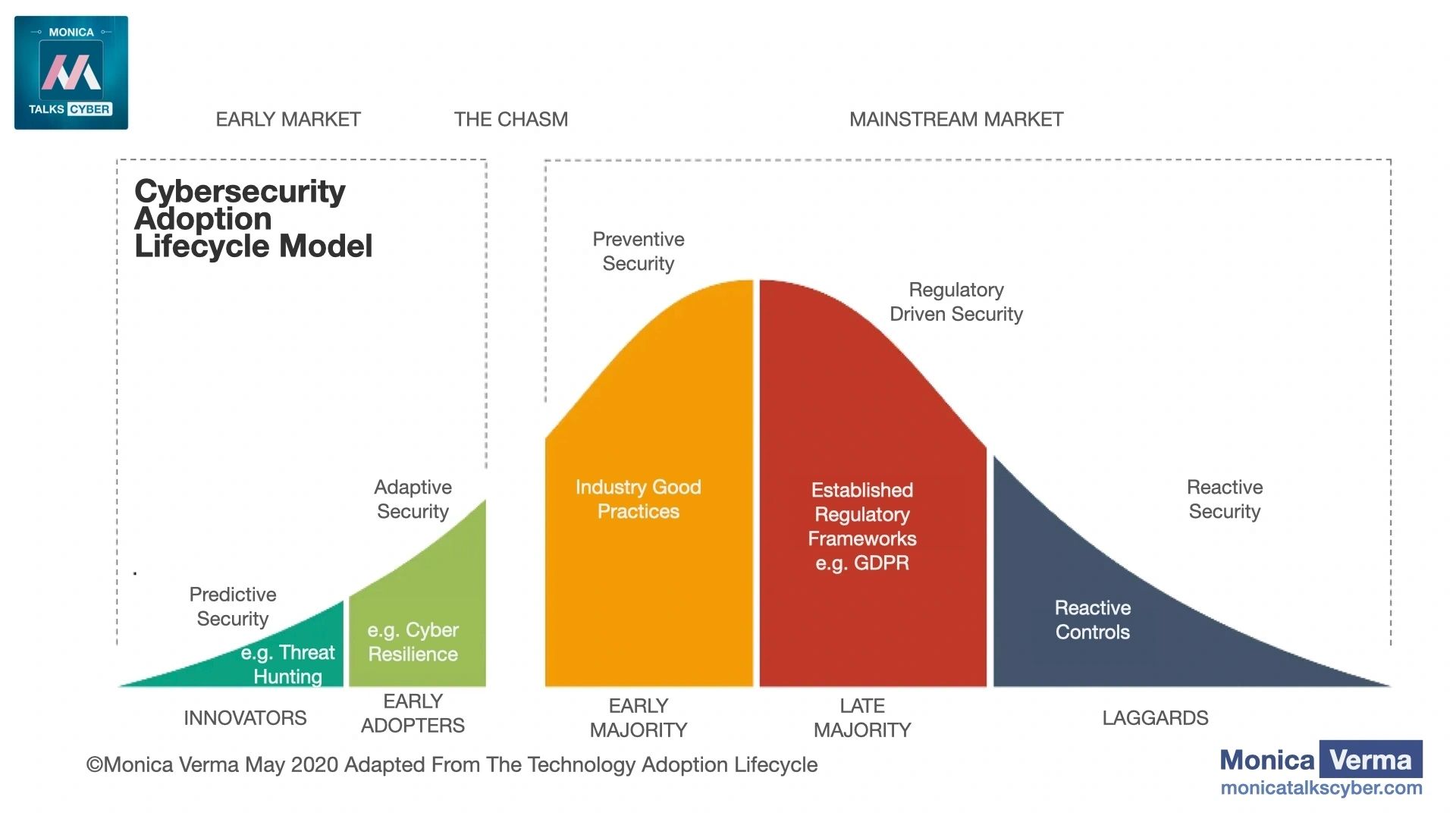
Building cyber and operational resilience requires effective planning and response to manage both the known-unknowns and the unknown-unknowns. Additionally, this takes into account people, processes, and technical aspects. Here are the key things organizations can do to build resilience over time:
a. Building resilience requires a clearly defined accountability at the top level as well as a resilient, collaborative, and prepared workforce. Accountability and awareness are key. Train your employees and train them regularly. It’s vital that the board and top-level management understand their accountability, as well as that every employee understands their role and responsibilities both during normal operations and an ongoing crisis. Test your preparedness and crisis management plans. Make sure your crisis management team works like a well-oiled machine. Run table-top exercises, learn and repeat.
b. Map, understand, and have a comprehensive overview of the dependencies that your critical services have on the underlying assets within your entire supply chain. Do your homework to have effective planning and preparedness in place. Build your crisis management and preparedness plans based on disruption scenarios for your business and critical services towards society, dependencies within your organization and on your third parties, your risk exposure, and your risk tolerance. Your crisis management plan should also take into account the steps you execute in case an unknown scenario occurs.
c. Invest in adaptive response management. As there are always unknown factors in play, an effective response management will include adaptive mechanisms, in addition to preventive controls. For example, can we activate certain policies in real-time as certain events or anomalies are detected? How can we fail-safe both within our IT and particularly our OT environments, while keeping critical services up and running? How do we adapt the use of our people, processes, and environment in real-time to reduce the impact? How quickly can we segment (parts of) our infrastructure, in order to contain the spread? How quickly do we predict a threat or detect an attack before it becomes a crisis? How do we reduce recovery time?
What are some of the technological disruptors to cybersecurity?
In my opinion, the top three technological disruptors to cybersecurity are:
a. Cloud
Cloud is no longer a new technology. However, the skyrocketed migration to cloud in recent years demands an urgent shift in mindset, especially when it comes to cybersecurity and privacy. Moving to the cloud is no longer just a lift and shift operation, even if that’s what you may be doing with some of your services and data. To effectively utilize the benefits of cloud computing, in a secure and privacy-friendly manner, a shift in the mindset is required right from the very beginning, integrated right from the planning stages of a migration, through operating in the cloud and all the way to the exit stage.
b. Convergence of physical, biological, and digital worlds
With the adoption of Internet of Things (IoT) and other emerging technologies, there is an even stronger convergence of the physical, biological, and digital worlds in progress. However, there is a big gap in understanding what risks this entails and the lack of management of these risks as a part of a cybersecurity strategy. As we go forward, there is a stronger need to address these issues at a strategy and business level to ensure that security, safety, and privacy continue to be a top priority.
c. Machine Learning and Artificial Intelligence
Machine learning and the emerging applications of artificial intelligence are some of the key technological disruptors, as ethics, safety, and other risks emerge along with it. We are already seeing Proof of Concept (PoC) cyberattacks enhanced by machine learning. As we go forward, these emerging technologies will be abused by cyber criminals and other threat attackers in various ways, including but not limited to, increased scale and effectiveness of cyberattacks, discovering new unknown vulnerabilities and exploits faster, bias, discrimination, and other ethical, security and privacy violations. As the threat landscape evolves, the use of machine learning and artificial intelligence within cybersecurity will be critical.
What are the elements of an effective cybersecurity program for critical infrastructure?
Due to the ongoing convergence between Information Technology (IT) and Operational Technology (OT) environments including Industrial IoT (IIoT), along with accelerated digitalization as a result of the pandemic, we have seen a massive rise in cyberattacks, particularly ransomware, against critical infrastructure. The key with critical infrastructure is operational resilience both during normal operations and under crisis. An effective cybersecurity program for critical infrastructure addresses three key areas:
a. Legacy systems within the OT environment
As the threat landscape and attack vectors have evolved, the convergence has left the legacy OT systems even more vulnerable to cyberattacks. Additionally, the lack of visibility and the difficulty of maintenance pose an even bigger threat as both old and new vulnerabilities and attack vectors are discovered. The basic cybersecurity hygiene e.g. patching, awareness and other preventive controls are even more important in the OT environment, as these systems get connected to emerging technologies. Hence, the basics is still one of the key aspects.
b. Over-increasing complexity and attack surface
Due to technological disruptions and ever-increasing convergence, both the complexity and the attack surface of OT environments including the critical infrastructure are increasing drastically. This increases the likelihood of a successful cyberattack, as the threat actors now have a much larger attack surface to begin with. Going back to the point, it’s not if or even when you’ll get hacked, but rather how quickly we detect, adapt, and respond to an attack. Hence, building operational resilience is a critical aspect to be addressed in an effective cybersecurity program.
c. Managing the consequences and risks to life, safety, and society
As with every cyberattack, a key aspect is to understand and contain the impact, as early and efficiently as possible. To do that, it is vital to have a comprehensive overview of what risks are associated with critical infrastructure, along with how it impacts the business, the organization, and society at large. As we move from traditional IT to OT environments, we switch from just talking about downtime or data breaches to risks to life, safety, and functions with society as a whole. A good security investment is always risk-based. This is even more vital for critical services, as the impact can be tremendous.
What are some of the key challenges with regards to diversity, inclusion, and equity within the cybersecurity industry and how can we address them?
We have seen an increasing awareness of diversity, inclusion, and equal rights over the last decades, both within society in general and in the cybersecurity industry. However, we still face massive challenges when it comes to pay grade, job requirements and hiring, reasons and motivations behind diversity and inclusion, as well as a lack of understanding of equity and the role it plays.
On one hand, we need to have continued conversations and take further actions for better representation within the cybersecurity industry. On the other hand, we need to do that while breaking down the labels and stereotypes. I am a CISO. Not a female CISO. My professional experience and contributions are independent of my gender, background, and other labels.
That means, while on one hand, we need definitive actions to reduce the pay gap, include diversified talent, and ensure effective and streamlined hiring processes including neutrally worded job positions with realistic requirements, on the other hand, we need to break down the barriers to bring in a diversified workforce independent of their labels. That includes diversity in both what we see and what we hear, i.e. diversity and inclusion of opinions.
Equity is yet another term that is highly misunderstood. Equity is not the same as equality. While equality is important and talks about equal opportunities and resources, e.g. equal pay grade, equity is about fairness, i.e. giving people what they need in order to make things fair and level the playing field. Due to stereotypes and lack of a balanced representation over decades, there is a need for equity to ensure we can reach equality. Equality is the end goal, but equity is the means to reach it. Equity is not about giving too little to people who need it or too much to those who don’t, but rather to provide fairness in order to reduce the differences of inequalities and pave the way to a more equal society and cybersecurity industry.
